Greetings

"Project for Establishing a Nationwide Practical Education Network for IT Human Resources Development - Education Network for Practical Information Technologies (enPiT)" is an educational program aiming at nurturing advanced IT human resources. The objective is to train students to solve real world problems through a unique program including specialized lectures and exercises organized
under the cooperation of universities and industries.
In the "security field (enPiT - Security)", 14 universities jointly launched the Basic SecCap program.
There is an urgent need for qualified personnel in the cyber security field. The program focuses on the development of practical skills. This is an effort to develop a practical educational program, which includes various teaching methods and is based on the collaboration between universities and industry or security related organizations.
Given the evolution of (mobile) networks and the threat of advanced information security, we need to train human resources with the necessary fundamental knowledge and practical skills necessary for risk management. The curriculum consists of "basic courses", "specialized courses", "practical courses", and "Advanced practical courses".
- "Basic courses": Acquire basic knowledge of information security.
- "Specialized courses": Master basic knowledge and advanced knowledge. It is carried out in four universities, and remote participation is also possible from other schools.
- "Practical courses": Use learned knowledge and acquire practical experience through practical exercises. There are multiple Problem Based Learning (PBL) courses available.
- "Advanced practical courses": Acquire additional practical experience. It consists of graduate school internships and advanced PBL courses.
This program can produce excellent human resources due to its specific structure: focus on practical experience (via PBL) and cooperation with industry.
Applicants who complete this course will receive a SecCap completion certificate.
About Basic SecCap
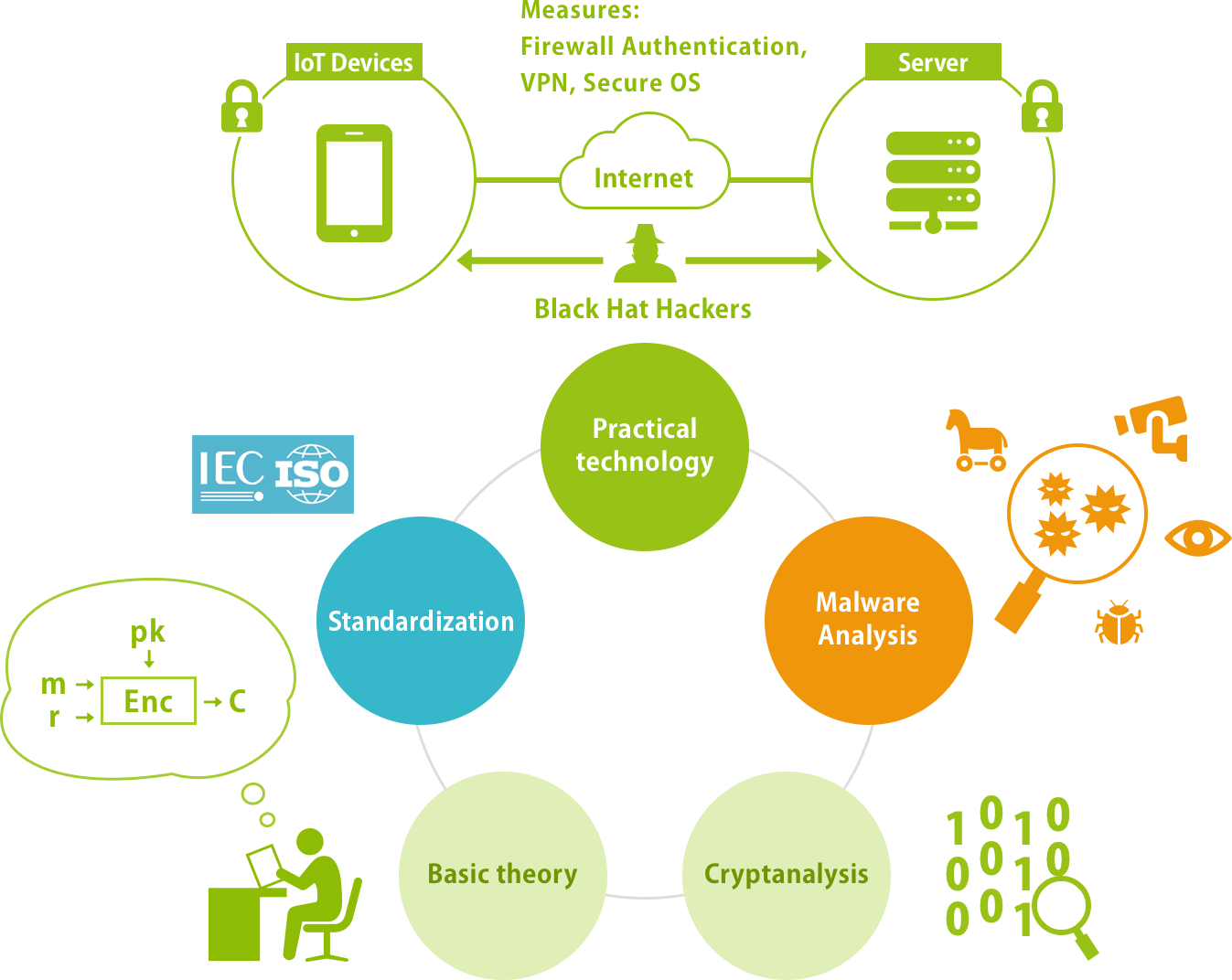
It aims to exhaustively cover the security field with two vertical axes. Specifically, from the "symmetric cryptanalysis" to the "malware analysis" and from "foundation theory" to "practical technology / standardization", it will cover contents of the latest information security technology widely such as the fundamental theory of security, cryptography, practice, and international standardization.
Special Subjects
Remote participation is also possible from other schools!
Foundations of Security
Practical courses
Remote participation is also possible from other schools!
Security PBL
- Exercise on privacy preserving protocol of big-data
- Construction of secure distributed networks
Advanced practical courses
Remote participation is also possible from other schools!
Advanced security PBL
- Implementation of Security Functionalities in Construction of Systems and Security Monitoring and Management
- Implimentation of secure elliptic curve cryptosystems for IoT devices
Basic SecCap course consists of three levels
- Basic SecCap 7、8、10 Certification
- SecCap 7 = Basic courses 4 points + Specialized courses 2 points + Practical courses 1 point
- SecCap 8 = Basic courses 4 points + Specialized courses 2 points + Practical courses 1 point + Advanced practical courses 1 point
- SecCap 10 = Basic courses 4 points + Specialized courses 2 points + Practical courses 1 point + Advanced practical courses 3 points (including at least one graduate school internship)
Special Subjects
Remote participation is also possible from other schools!
- Instructors
- Mitsuru Matsui、Yu Arai、Keisuke Takemori、Atsuko Miyaji、Akinori Kawachi
In this lecture, students will learn the following important topics in cyber security area as a specialized course of Basic SecCap Course.
Foundations of Security
Understanding Cryptography from Mathematical Modeling Perspective
In cryptographic technology such as public-key cryptosystems, it is indispensable to guarantee "no leakage of secret information." So, how should we guarantee it? In this lecture, we study how to model cryptosystems and analyze their security mathematically by an approach from fundamental theories of the information science.
Information Security from an algebraic point of view
The principle of security technology, its secrity proof, and the efficiency is based on various theorems in algebra. How we use algebra in practical information security? By acquiring techniques to apply complicated algebraic theorems to practical information security, we aim for practical acquisition of algebra that enables construction of another security technology.
Exercise for Security Evaluation and Implementation of Practical Cryptosystems
We study fundamental notions of symmetric-key cryptography (such as block ciphers, stream ciphers, modes of operation, message authentication, etc.) and ideas of security evaluation for symmetric-key cryptosystems with specific application examples
Malware Analysis by Python
We study techniques for malware analysis, which is a one of skills more highly rated as engineers in the real world. In particular, we understand the techniques and then master them by nearly hands-on exercises.
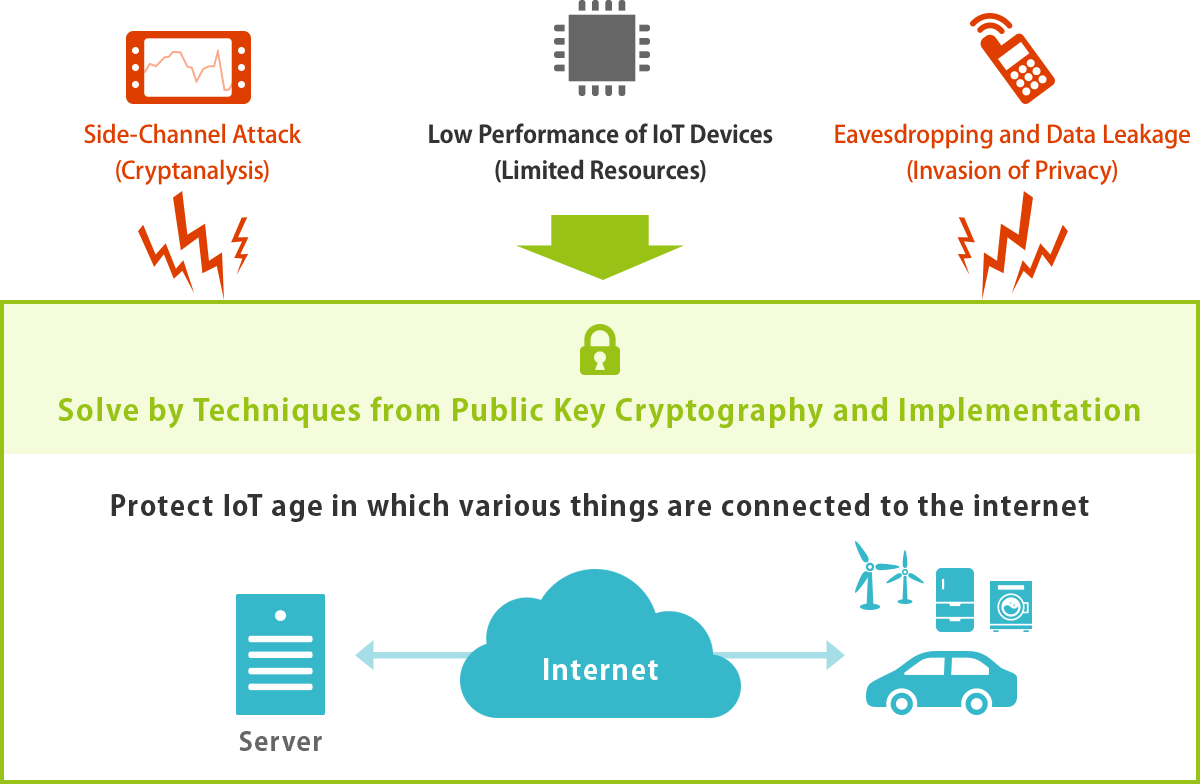
IoT Devices and Their Cybersecurity
The era of the Internet of Things (IoT), in which everything connects to the Internet, is coming. We study securing devices and security countermeasures for communication to provide against cyberattacks by reviewing past incidents. In particular, we consider primitives that protect connected cars and general IoT devices.
International Standardization
Standardization is indispensable for dissemination of security technology. We study how to standardize security technology using concrete examples.
Practical Courses
Remote participation is also possible from other schools!
※Get 1 point from the follwing lectures(each of them gives 1 point)
Security PBL ISpring~Summer, Intensive Course
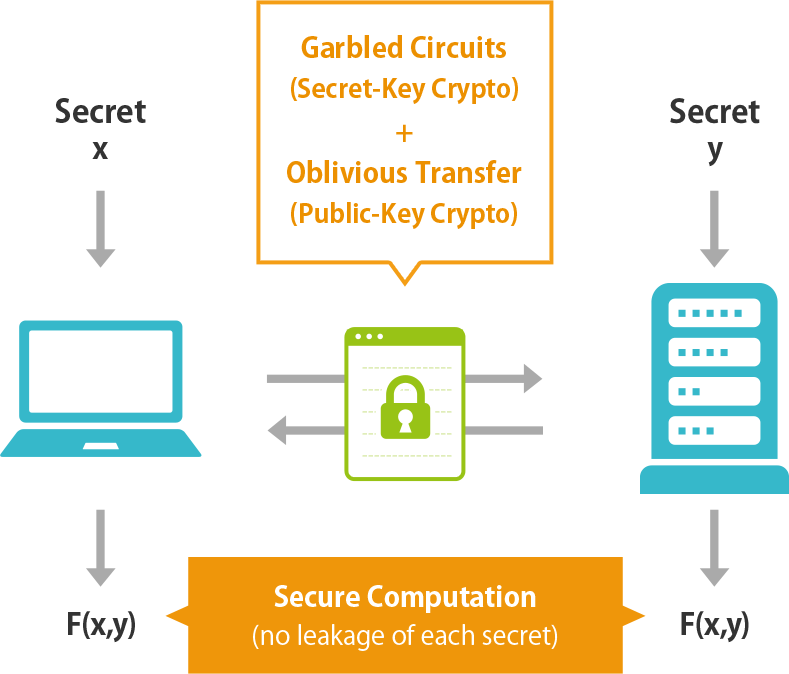
Exercise on privacy preserving protocols on big-data
In the big data analysis such as applications to diagnosis of analyzing results of medical data collected from many patients, it is important to preserve privacy of the individuals. In this course, we aim at understanding the principle of the secure computation as a crytographic foundation and its components such as garbled circuits, oblivious transfer, symmetric-key cryptography, and public-key cryptography through lectures. We also learn how to implement the cryptographic technology through exercise.
Security PBL IIAutumn~Winter Intensive Course
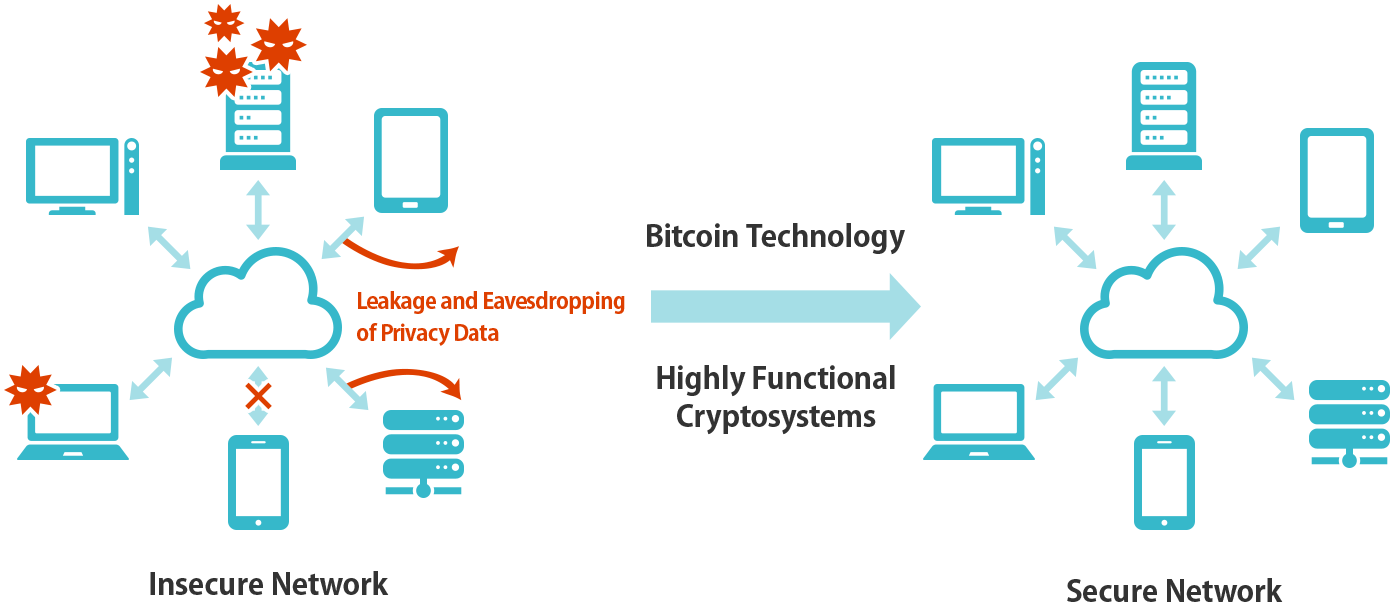
Construction of secure distributed networks
Students will learn techniques for constructing secure applications in distributed networks for integratedly and securely using data in many cloud servers.
※Requirement/Prerequisite:Students are expected to take "Foundations of Security".
Advanced Practical Courses
Remote participation is also possible from other schools!
※Get 1 point from the following lectures(each of them gives 1 point)
Advanced security PBL ISpring~Summer Intensive Course
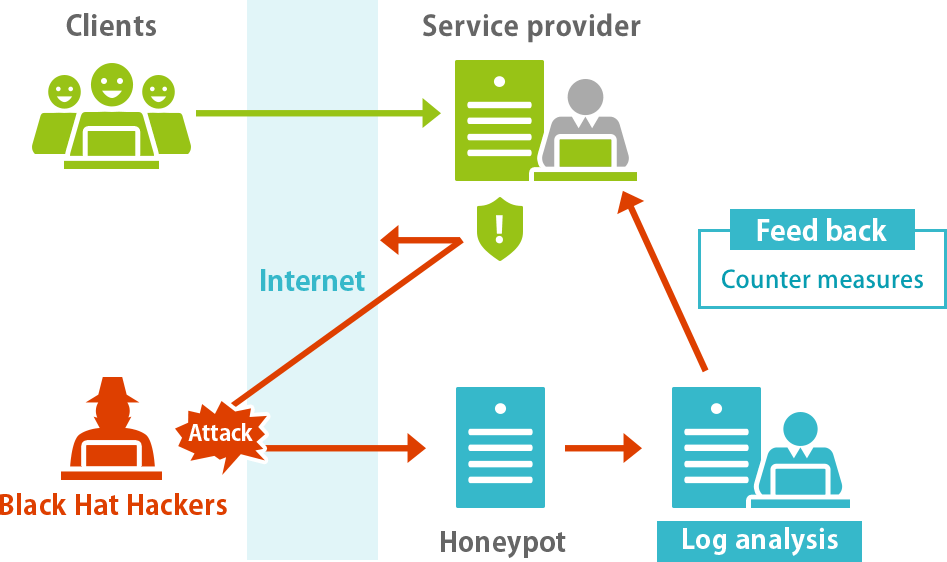
Implementation of Security Functionalities in Construction of Systems and Security Monitoring and Management
Students learn how to define requirements of security functionalities and how to implement details of functionalities for practical systems in industries. Students also understand how to monitor and manage security of systems by log analysis.
※ Requirement/Prerequisite: Students have to take the course "Information Security B". Students are expected to have fundamental knowledge of ICT (e.g., Servers, OS, Windows, Linux, Routers, etc.), of TCP/IP communication, (IP address, DNS, etc.) and security (DDoS Attacks, Ransomware, etc.).
Advanced security PBL IIAutumn~Winter Intensive Course
Implementation of secure elliptic curve cryptosystems for IoT devices
Students will learn how to implement cryptographic techniques, especially elliptic curve cryptosystems, which are applicable under limited resources of IoT devices.
※ Requirement/Prerequisite: Students have to take the course "Information Security B".
Basic Courses
※Get 4 points from the following lectures for 1st - 3rd year students (each of them gives 2 points)
Mathematics for Information and Communication Systems I
Instructor:Tetsuya TAKINE, SAMPEI SEIICHI情報通信工学に必要な基礎数学(確率、線形代数、代数)の講義を行う。
Mathematics for Information and Communication Systems II
Instructor:Takao OnoyeSo as to improve the students' ability of designing efficient algorithms for solving problems in the areas of computer science and system design, the lecture introduces efficient algorithms for combinatorial problems, and describes basic techniques for algorithm design.
Probability and Statistics
Instructor:Shunsuke SaruwatariProbabilistic or statistical treatment of various phenomena and data associated with nature and society is a widely used approach. The knowledge of probability and statistics is indispensable in the planning of various surveys, measurements, and laboratories, result evaluation, and reliability evaluation. The lecture describes: methods for preparing data; and basic concepts of probability and statistics, such as random variables, typical probability distributions, statistical estimation, test, and variance analysis. With examples and applications in the field of electronic, information systems and energy engineering, the students acquire the ability of applying the knowledge into practical problems.
Database Engineering
Instructor:HARUMOTO KANAME, Takahiro HaraThe management of a large amount of data is one of the most important purposes for utilizing computer systems. So far, various technologies and techniques have been developed in the field of the database management systems. In this course, the student learns fundamental technologies and techniques of database management systems, by which the student learns the importance of the database systems. Especially, by focusing on relational database systems, the notion of data model will be presented and the query processing mechanism will be explained. The syntax of the SQL, which is the standard query language in relational database systems, will be presented and practiced.
Software Engineering
Instructor:Yasuyuki Matsushita, Yuusuke Sugano, Masaki SamejimaThe methods for planning, designing and developing large-scale software are covered in this course.
Computer Science and Programming I
Instructor:SUGIHARA HIDEHARU,MORIFUJI MASATO,TATSUMI KEIJIThe students perform exercises in programming in C language, and learn practical and advanced programming techniques in data processing and technological computation.
Computer Science and Programming II
Instructor:Takahiro Hara,IBI Shinsuke,Yuki AraseComputer programs written well are easily understood and efficiently executed, whereas poorly written ones are unreadable and consume time and memory. In this lecture, the students learn the essentials for writing good programs. More specifically, the lecture discusses: basic algorithms used often in various computer programs; and data structures permitting these algorithms to run efficiently. Throughout this lecture, much attention is focused on writing well-structured and easily understood programs and on evaluating computational complexity in the programs. The lecture gives the basics of these themes. The students also perform exercises in programming in C language, and learn practical and advanced programming techniques in data processing and technological computation.
Fundamentals of Information and Communication Systems I
Instructor:Takashi WatanabeThe aim of this course is to provide Shannon information theory and coding theory for quantitative expression of information, and basic concepts of information source and effective transfer of information. It starts with definitions of fundamental concepts of entropy, mutual information, and theorem of source coding with specific coding methods. Then, theorem of channel coding on error-prone channels with specific coding methods are given.
Fundamentals of Information and Communication Systems II
Instructor:MATSUDA TAKAHIROThe lecture addresses telecommunications networks which form the foundation of highly information-oriented society, and describes transmission and switching technologies and network protocols serving as the basis of the networks. The lecture mainly focuses on computer networks, so that the students learn the basic technology of widely used communication networks such as the Internet.
Compiler
Instructor:Onizuka MakotoMost of the IT systems in real world, such as those used in the Internet or cellar pones, are implemented by programming languages. Those languages are compiled into executable codes by compilers and then they are deployed as IT systems. The objective of this course is to study the theory and practical usages of the compilers.
System Programs
Instructor:Susumu Date, KOJIMA KazuhideOperating system (OS) is designed to optimize computation performance as well as make computer systems more user-friendly. This is an introductory course on the basics of operating system and system programming.
Discrete Mathematics and Theory of Cryptography
Instructor:Atsuko Miyaji・情報セキュリティにおいて必要となる離散的な構造に対する数学的諸概念や考え方に習熟する。
数学的な概念のセキュリティへの応用について学ぶ。特に、暗号の基本原理、手法、安全性証明、計算効率の習得を通じて、数理的な考え方及びその応用方法について理解することを目的とする。
Computer System and Logic Design I
Instructor:KAMAKURA YOSHINARI,MORI NOBUYA,Taniguchi IttetsuThis lecture aims to learn fundamental knowledge on computer hardware. The lecture reviews the theoretical basics and design techniques of "logic circuits" constituting computers, operation circuits, control units, and the like, and describes the basic knowledge of logic algebra, number representation, and computers.
Computer System and Logic Design II
Instructor:MATSUOKA TOSHIMASA,Katsuyoshi Miura This lecture aims to learn fundamental knowledge on computer hardware. The lecture reviews the theoretical basics and design techniques of operation circuits, control units, and describes the basic knowledge of number representation, and computers. The lecture intends to to understand the logical structure of computer, particularly the hardware construction of computer and the functions of the components.
Information Theory
Instructor:Akinori Kawachi The cource objective is to deeply understand the information theory, which provides mathematical foundations of information communication technology in the advanced information society. In particular, we learn representative results of the information theory such as the source coding theorem for data compression and the channel coding theorem for communication efficiency, and important applications of the information theory to other fields.
Information Literacy C
Instructor: Hideyuki Andou We aim to acquire the ability to utilize information such as information transmission, collection, organization, analysis. We will practice basic usage of information literacy, e-mail, WWW (World Wide Web), TeX. We will proceed with exercises while actually touching a computer about various operation methods of the calculator and knowledge when using the calculator. Simple programming Understand the programming concepts and basic techniques through C language.
平成28年度以前入学生については「情報セキュリティ」、「離散数学」、「ソフトウェア工学」、「コンピュータサイエンスとプログラミング」、「コンピュータシステム」も基礎科目に含まれる。
Schedules
準備中